Critical national infrastructure is an increasingly attractive target for state-sponsored activists and extremist groups. Remote infrastructure – everything from outstations to wind farms, wellheads to pump stations, haul roads to transport hubs – is particularly vulnerable because of the challenges in creating robust security solutions in these locations. This blog post seeks to present a solution to these challenges, but first, let’s dig into the issues in more detail.
The Growing Threat to Remote Infrastructure
The vulnerability of utility and energy production sites to cyber attacks is well documented; from 2023 to 2024, US-based utilities experienced a 70% surge (Reuters). Less frequently reported is that physical attacks on infrastructure also rose 73% from 2020 to 2022 (Axios), with incidents including a gunfire attack on two substations in North Carolina, USA, which left 45,000 customers without power.
In Nigeria, in early 2024, the power sector faced escalating vandalism of high-voltage transmission infrastructure; incidents tripled during a 15 week span, including explosives being used to destroy transmission line towers (The Electricity Hub).
In Australia, thefts from unmanned construction sites reached a 10 year high in September 2024, with a 22% increase in theft-related offences during the same period (Herald Sun). And in the UK, the cost of theft of agricultural equipment escalated to an estimated £52.8 million in 2023, a 4.3% increase from the previous year (NFU).
In addition to a growth in isolated incidents is the underlying strategy to destabilize infrastructure, driven by alliances between state actors like Russia, and organized criminal gangs. These activities include sabotage, arson and cyber attacks, aimed at undermining critical infrastructure (The Guardian).
Attacks are increasing: companies, governments and individuals with hard-to-protect, high value assets are fighting a rising tide of criminal activity.
The Challenge of Traditional Security Measures
The infrastructure we’re describing here – transport, energy production, heavy industry – operates across vast areas, making it impractical to station physical security at every location which could be a target. Assuming a single security guard is stationed at a site for 8 hours a day, 7 days a week; the cost of an unarmed guard would be c. $3,600, and c. $6,000 for an armed guard (Deep Sentinel).
Statistically, most theft takes place after dark, and are more frequent in winter; long weekends and holidays are also attractive (Site Watch Group). Thus, 24 hour cover would be prudent at least over weekends, adding substantially to the cost.

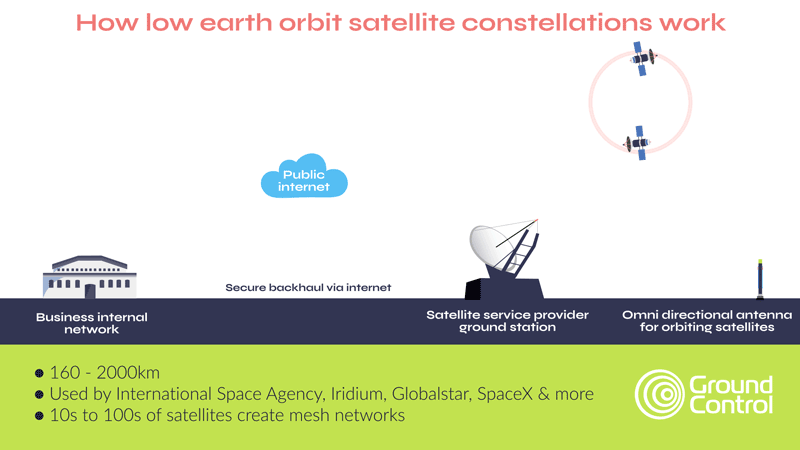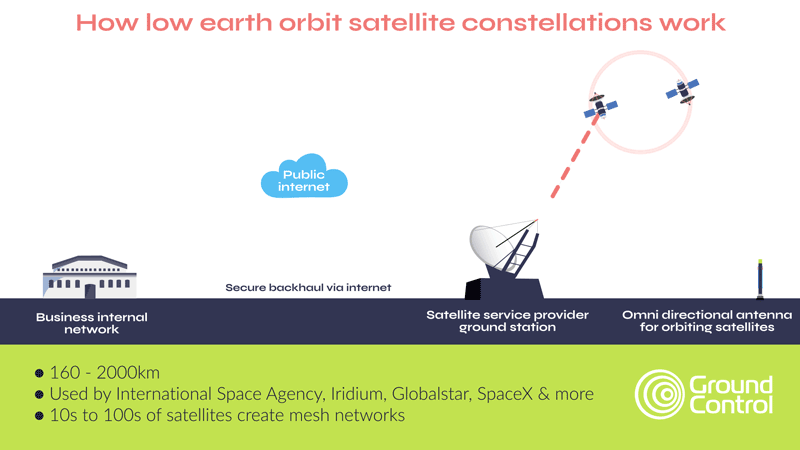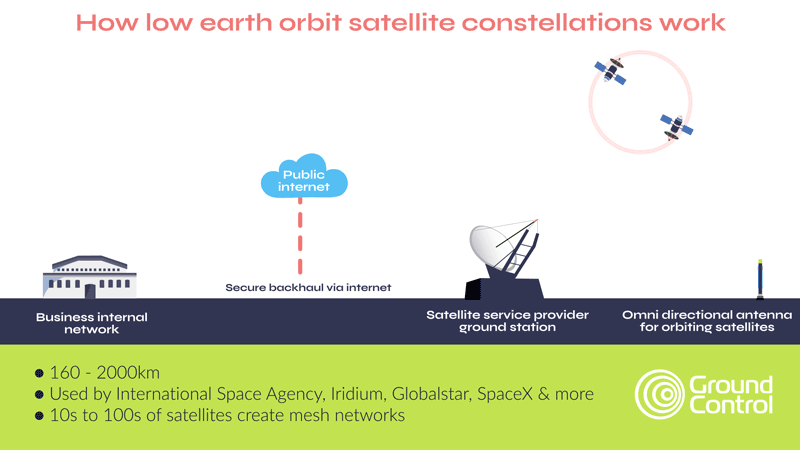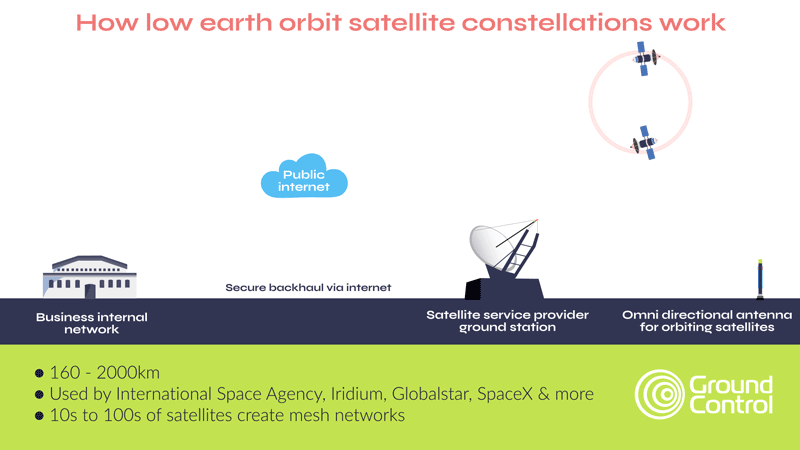
Another option is to use fences coupled with cameras and sensors to detect intruders, and provide real-time alerts to a remote monitoring center. The security personnel there can monitor multiple sites remotely, reducing on-site staffing costs. Upon receiving an alert, they can choose to dispatch security personnel to the affected site, alert local law enforcement or trigger some localized deterrent such as alarms, voice sirens or lights.
The pros of this approach is that it’s lower cost, delivers 24/7 surveillance, and can be rapidly and cost-effectively scaled up. However, it requires a reliable, secure and cost-effective means of transmitting the video stream (and potentially also audio and movement sensors). Within cellular connectivity this is pretty straightforward, but in a remote site, satellite is often the only viable option.

Finding the Right Satellite Connection for Remote Surveillance
Satellite connectivity isn’t a homogenous blob. There are multiple radio frequencies used, and the type used strongly influences the form factor of the satellite transceiver. For example, people seeking broadband internet access over satellite – Starlink, Hughesnet, OneWeb etc. – will be using Ka-band, as this supports higher data rates, and there’s plenty of bandwidth available (i.e. limited congestion issues).
The drawback of Ka-band is that it is both susceptible to rain fade (signal loss in bad weather), and the antenna size is large, power hungry, and needs to be precisely positioned. This is not an issue for home installation, but in a remote outstation, there may be mountains, trees or the outstation itself preventing the ideal siting of the antenna.
The fix to this – phased array antennas which electronically steer themselves to optimal positions – has the drawback of consuming significantly more power. Indeed, it would be challenging to power any Ka-band antenna via a solar-powered battery, particularly for the sorts of continuous operation that a surveillance system requires.
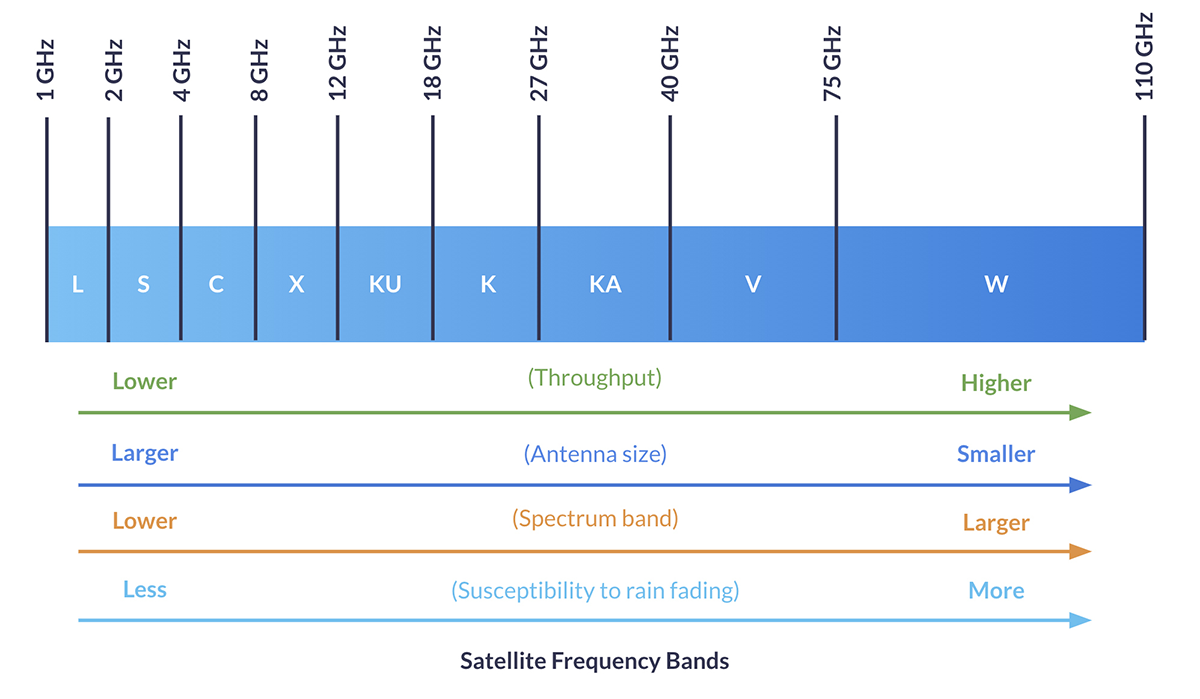
Satellite services that operate in the L-band spectrum, on the other hand, have very small antennae, and low power requirements compared to Ka-band. Iridium and Viasat (previously Inmarsat) utilize L-band for data transmission, which makes them perfect for IoT applications where the data requirements are lower, and a small, discreet, battery-operable antenna is an asset – sometimes a necessity. L-band transmissions are unaffected by weather conditions, and very hard to intercept, making them ideal, in principle, for mission critical applications like remote surveillance.
However, video streaming from remote, potentially unpowered locations, is an awkward fit for both Ka- and L-band. It’s a high bandwidth transmission, but as discussed, high bandwidth satellite services are power hungry, easy to identify (and therefore to put out of action), and difficult to position. L-band fixes all those challenges, but to send video over L-band, which is a much more constrained frequency band, is very expensive.
Until now…
A Breakthrough in Remote Video Surveillance
There have been two key developments that have made it possible to send video over an L-band satellite connection cost-effectively. The first is the advent of low bandwidth video. Our partner Videosoft has developed video compression and transmission technology that delivers real-time, low-bit rate video. They’ve coupled this with an image enhancement feature that lets users specify and download high-res pixels from an area of interest in a scene.
Videosoft’s technology works with most off-the-shelf hardware, including video cameras, CCTV, audio microphones, GPS tracking antennae, and other I/O devices.
Watch Videosoft Demo
The second development is the availability of midband (higher throughput) transmissions in the L-band spectrum; notably Viasat’s IoT Pro service, and Iridium’s Certus 100 service. The latter is particularly well suited to remote surveillance because the satellites are in Low Earth Orbit, which means the latency is very low – critical when you need real-time alerts if a facility has been penetrated, or an asset is moving outside of schedule.
Additionally, Iridium has a cross-linked network of 66 satellites, which means you don’t need to point your antenna at the satellite; if your facility or asset is in a wooded or mountainous area, this could be a critical advantage.
RockREMOTE Rugged: A Simple and Secure Solution
There are a number of Iridium Certus 100 transceivers available – we design and build several ourselves – but the one we’ve focused on for remote surveillance is the RockREMOTE Rugged. This is because, most importantly, it has the compute power to natively run the Videosoft program without needing any additional hardware. It’s simply a matter of plugging your camera into the RockREMOTE, and working through some simple config steps to get started.
RockREMOTE Rugged is very easy to install; it’s IP67 rated, and designed for permanent outdoor installation in harsh environments. Its omni-directional passive antenna is small and discreet, making it harder to identify by bad actors.

Thus, securing a remote site becomes smarter and more cost effective. Choose from a very wide range of cameras, audio equipment, motion detectors etc., then plug them in to the RockREMOTE Rugged. The onboard Videosoft technology will compress the data so it can be sent cost-effectively over the Iridium Certus 100 network, in real-time, to your remote monitoring center.
A Smarter Approach to Remote Security
Protecting remote infrastructure has never been more critical – or more challenging. While traditional security measures struggle to balance cost and coverage, the combination of low-bit rate video, real time image enhancement, and power efficient satellite connectivity presents a game changing solution.
With RockREMOTE Rugged and Videosoft’s technology, organizations can deploy surveillance systems that are reliable, cost effective, and optimized for remote environments. Whether safeguarding critical national infrastructure or protecting high value assets, this technology ensures security teams have the visibility they need, when they need it most.
Smarter Security for Remote Infrastructure
Protect your critical sites with real-time video surveillance over satellite. Our RockREMOTE Rugged, combined with Videosoft’s low-bandwidth streaming, delivers cost-effective, 24/7 monitoring, even in the most challenging locations.
Complete the form, or email hello@groundcontrol.com to learn more. We’ll reply to your inquiry within one working day.






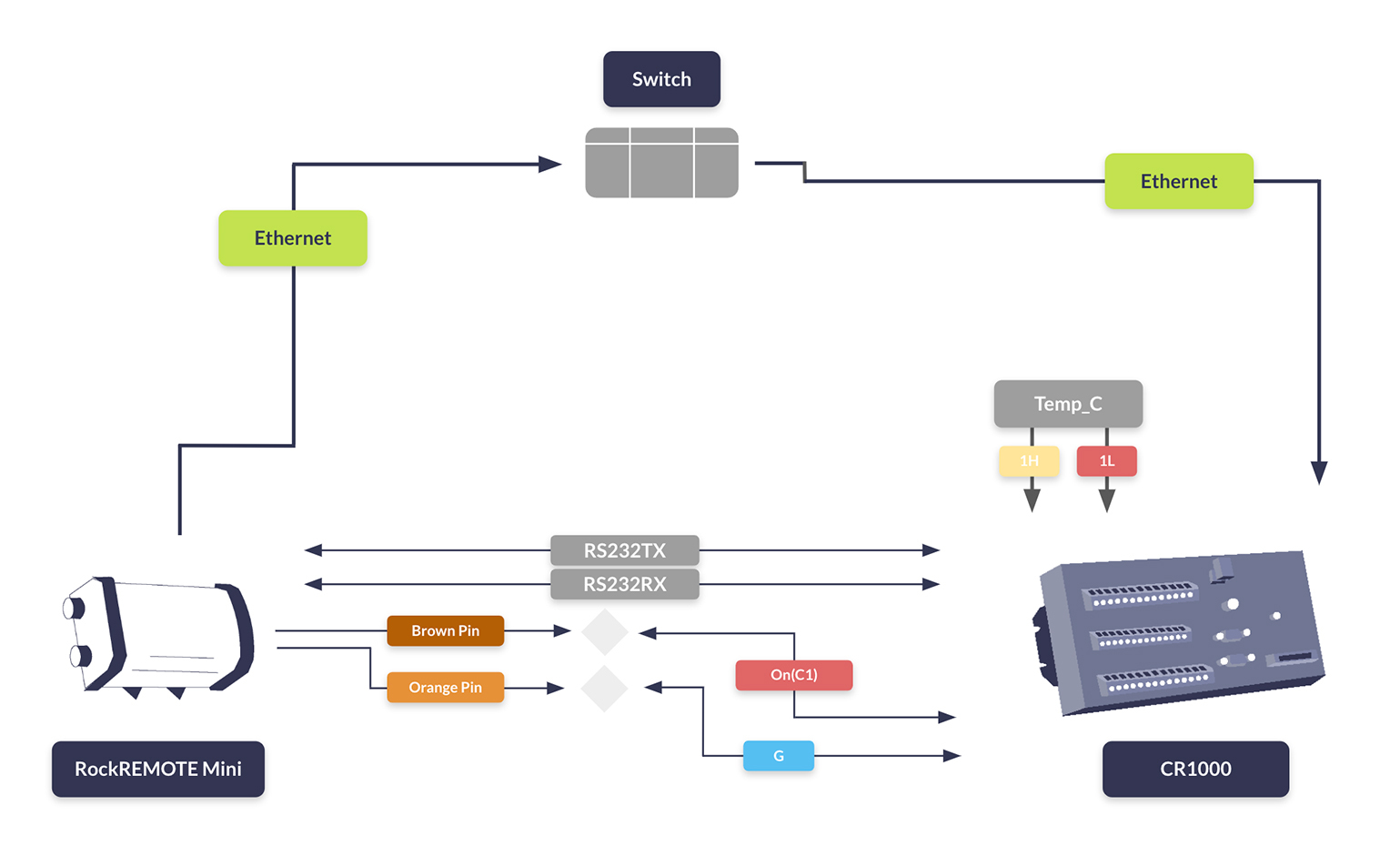

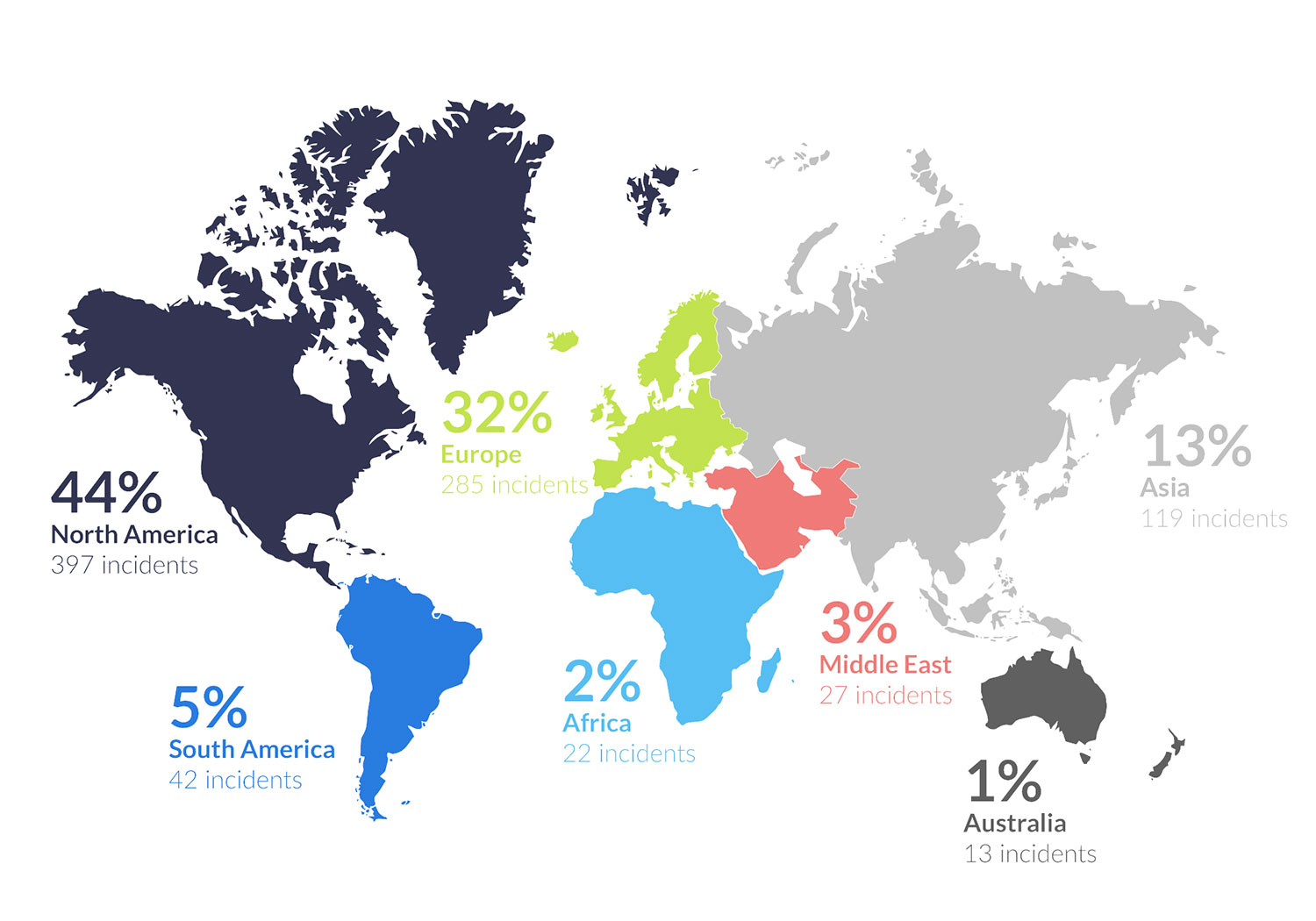 Illustration showing the number of reported ransomware attacks by continent
Illustration showing the number of reported ransomware attacks by continent