The IoT M2M Council recently reported a potential threat to “millions of routers and IoT devices”; malware named BotenaGo, identified by Alien Labs. This comes after a Zscaler report that IoT malware attacks rose 700% during the pandemic, 59% of which came from devices in manufacturing and retail.
Fortunately, there’s plenty of great advice to help mitigate the threat of IoT malware, and we’ve adapted this specifically for relevance to satellite IoT.
1. Monitor network traffic and unreasonable bandwidth usage
Can you review and analyze the amount of data each device in your network is using? Can you set alerts to ensure any unauthorized or unexpected data surges are shut down quickly? There are solutions available today that make this easy, such as Cloudloop; investing in one of these won’t prevent attacks but they will help you limit the damage.
2. Ensure minimal exposure to the internet / isolate IoT networks
Most satellite IoT users, whether you’re using satellites in low earth orbit (LEO) or geostationary, retrieve your data from your satellite service provider’s ground station using the internet at some point – and you have choices over how secure you make that connection. For example, this diagram shows a very simplified networking diagram for the RockREMOTE, a satellite IoT connectivity device.
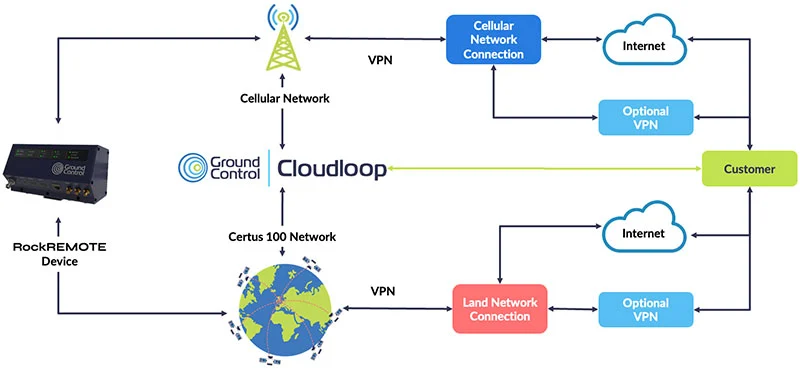
After the data from either the satellite or cellular network is sent to the land network connection, users choose between delivering that data via the internet, or using a VPN; the latter minimizes your exposure to the internet and is recommended for critical applications.
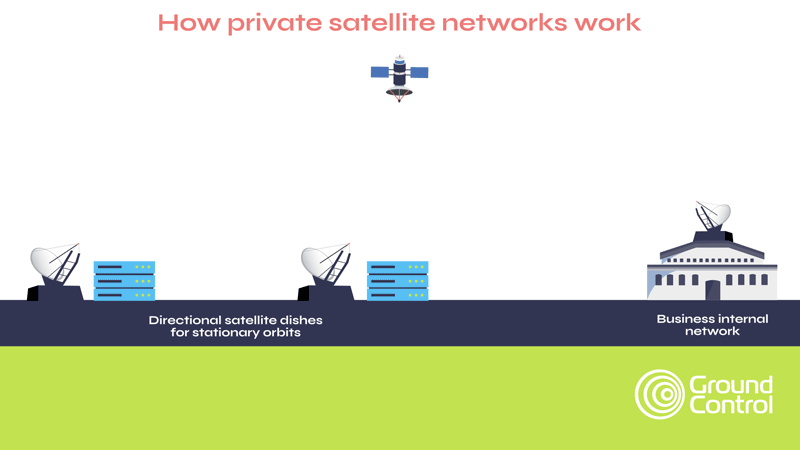
There is a further option for companies concerned with critical national infrastructure, such as Oil & Gas and Utilities, and that is to operate an entirely private networking solution. This service, from TSAT, is designed specifically for SCADA / telemetry networks, and essentially places a ground station at your premises; it does not use any public infrastructure connectivity such as the internet.
Further, the TSAT system has many features to prevent unauthorized access to traffic communicated via the satellite link, regardless of the traffic type (TCP/IP or serial), including the option of AES-256 encryption. In our view, it’s certainly worth exploring. The hardware is more expensive than your average satellite connectivity device, but once you’ve taken into account the simplified networking and lower data transmission costs, it can deliver, and has delivered, lower operating costs.
3. Use a properly configured firewall
An effective firewall will protect against:
- Network threats: DDoS (Distributed Denial of Service) and application-layer attacks which may disrupt the integrity and availability of the Service Provider’s network.
- Device threats: preventing devices from connecting to unknown services. This reduces the chances of devices being compromised.
- Service abuse: preventing IoT devices from being used unexpectedly, which can result in revenue leakage for the Service Provider or the application owner.
4. Update your passwords
Clearly not specific to satellite IoT but this is such an important point, we couldn’t leave it out. Remember, the infamous Colonial Pipeline hack in April 2021 was made possible because of a single compromised password which allowed the hackers to gain entry through an (unused but still viable) VPN account.
If you could use some objective advice on improving the security within your satellite IoT network, please get in touch with the Ground Control team. We have customers providing critical national infrastructure services globally, and have delivered secure, reliable connectivity in multiple applications.
Get in touch
We'd be happy to talk to you about your project and offer impartial advice on the best antenna and satellite service for your particular requirements. Call or email us, or complete the form.