In today’s interconnected world, digital threats have reached a scale never seen before.
In 2023, rising global tensions led to a surge in cyber threats and disruptions to critical infrastructure worldwide. Escalating conflicts – such as those involving Ukraine and Russia, Israel and Hamas, and nations in the South China Sea – motivated hackers to exploit critical infrastructure for control and financial gain. Globally, ransomware incidents are increasing across every continent, as the map shows. At the same time, ransomware attacks targeted more industrial organizations, with reported incidents increasing by nearly 50 percent [Dragos report 2023].
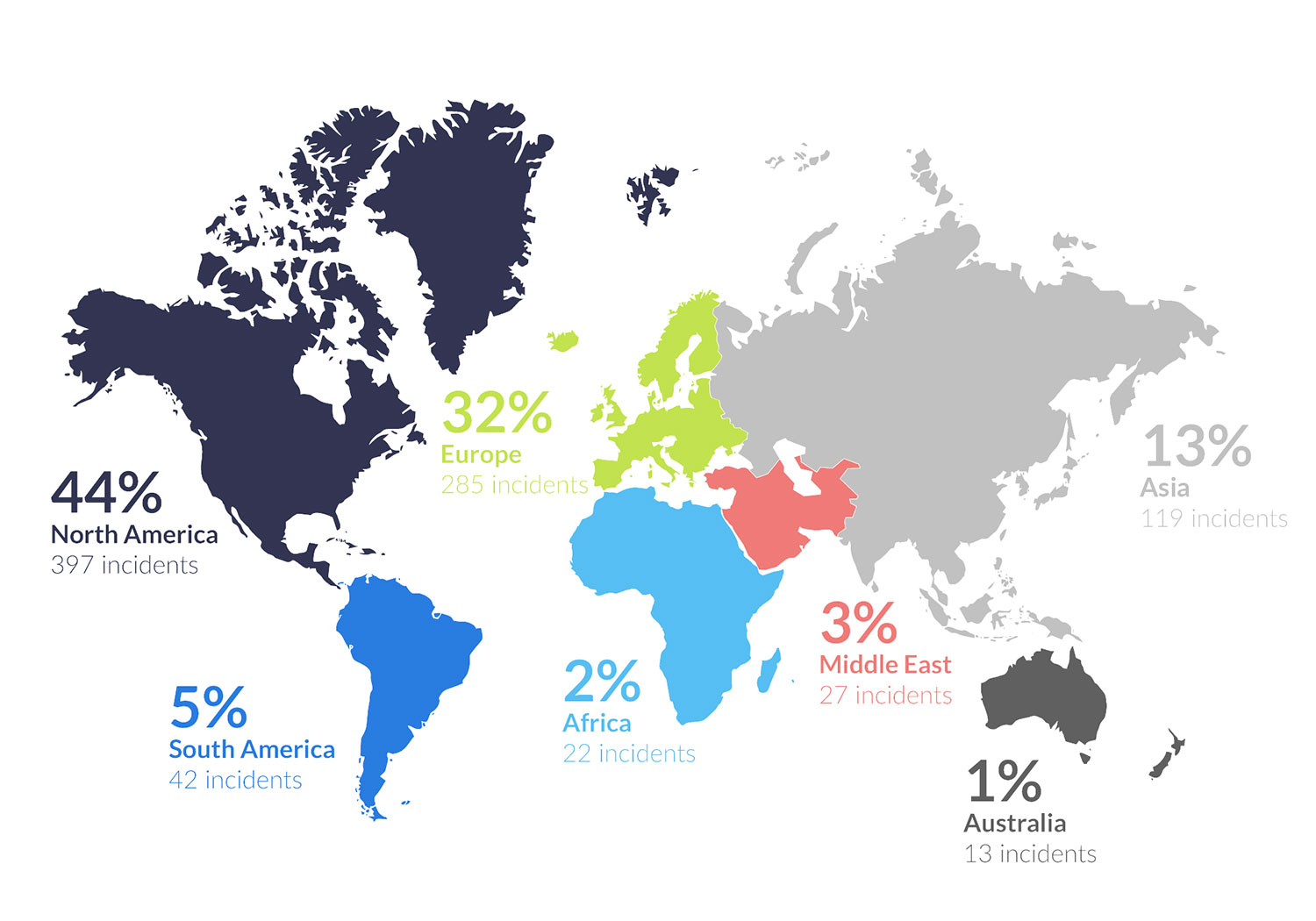 Illustration showing the number of reported ransomware attacks by continent
Illustration showing the number of reported ransomware attacks by continent
Cyber attacks can target everything from financial institutions to healthcare systems, transportation networks and power grids – and it’s of increasing concern to the general public. In January 2025, Ground Control conducted a survey of 500 US adults which revealed that over 65% were concerned about cyber attacks on critical national infrastructure, with 70% having limited to no confidence that essential services are protected from cyber attacks.
Utility providers are now facing an alarming new reality where cyber attacks increasingly threaten the safety of their operations. Indeed, Utilities is the second most targeted industry for ransomware attacks, experiencing a 270% increase in data violation cases between 2020 and 2023.
The 2021 Colonial Pipeline Attack
The 2021 Colonial Pipeline attack served as a wake-up call, underscoring the vulnerability of the utility sector to cyber threats. Hackers used a virtual private network (VPN) to infiltrate the pipeline’s control systems, causing widespread fuel shortages across the US East Coast. The incident led to a ransom demand of $5 million, which was ultimately paid to regain control of the pipeline.
The financial costs of data breaches are staggering. According to IBM’s 2021 report, the average cost of a data breach rose to $4.24 million. These costs go beyond the immediate exposure of data and include downtime, loss of revenue, and long-term reputational damage. Utilities must be proactive in defending against such threats to avoid crippling financial losses and operational disruptions.

The Hidden Vulnerabilities in Utility Networks
Utility companies depend heavily on SCADA (Supervisory Control and Data Acquisition) systems to monitor and control infrastructure. These systems collect and transmit data from Remote Terminal Units (RTUs), often located in remote or hard-to-reach areas. However, these RTUs present a significant security vulnerability. With 90% of utility customers reporting “limited to no visibility” into their industrial control systems, once a hacker gains access, they can easily monitor, manipulate, and potentially sabotage critical infrastructure [Dragos report, 2020].
It’s crucial for utilities to address this blind spot and implement solutions that safeguard the data extracted from RTUs and transmitted to SCADA systems.
How Remote Sites Become Prime Targets for Cyber Attack
Remote utility sites, such as offshore wind farms and oil and gas pipelines, are particularly vulnerable to cyber threats. With limited or no access to terrestrial connectivity such as cellular or fiber networks, these remote locations are often the last to receive attention when it comes to cybersecurity. Cybercriminals exploit this vulnerability, targeting sites that lack secure and reliable communications infrastructure. The risk is further compounded by the fact that many utility providers rely on lone workers or contractors to maintain and monitor these remote operations, leaving these sites exposed to cyber threats.
The Role of Satellite Connectivity in Improving Data Security in Utilities
Satellite connectivity has some inherent advantages over cellular networks when it comes to data security; with limited ground infrastructure, it’s less susceptible to physical attacks, and signals are more difficult to intercept. There’s also a reduced risk of infiltration via local Internet Service Providers (ISPs) as these are typically bypassed by satellite communications. But with satellite services diversifying, and more networks being launched, there are now many varying options for data security.
Our Recommended Solution
TSAT is a satellite-based communication system designed specifically for secure, resilient remote monitoring and control of SCADA systems. Unlike traditional ground-based communication networks which can be easily compromised by cyberattacks, the TSAT satellite communication solution provides a more secure and tamper-resistant infrastructure.

How TSAT Protects Critical National Infrastructure
The ability to remotely monitor and control systems via satellite communication is essential in maintaining the integrity of critical infrastructure. TSAT’s secure transmission capabilities ensure that communication between central control centers and field sites remains uninterrupted, even in the face of large scale cyber threats.
As mentioned earlier, satellite connectivity has several security advantages over terrestrial networks; a reduced attack surface, plus limited reliance on the public internet to move data being two examples. However, most satellite networks, whether in low earth orbit or geostationary orbit, leverage the internet to move data from the ground station to your application. This process iprotected via VPNs and firewalls, which, in addition to AES-256 encryption of data, satisfies most organizations’ requirements.
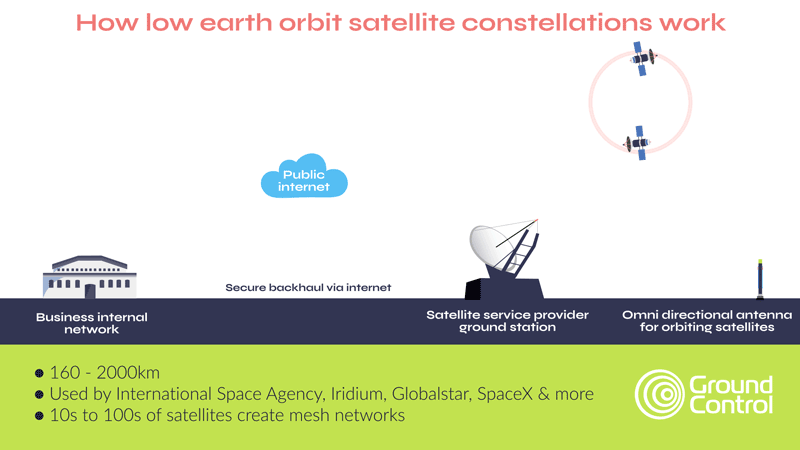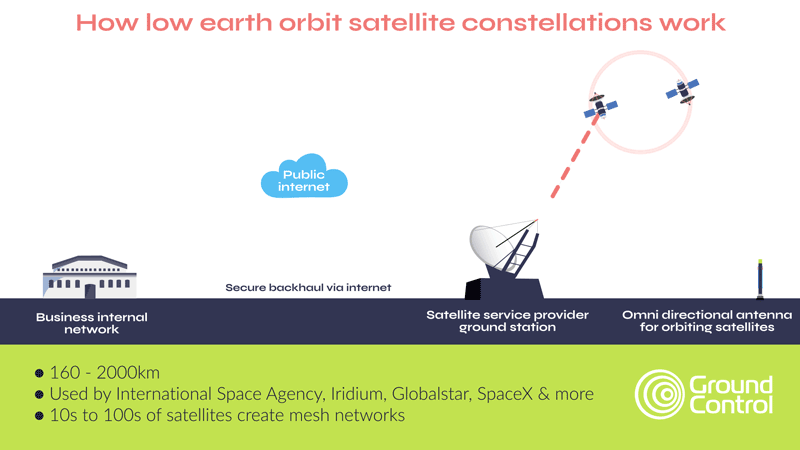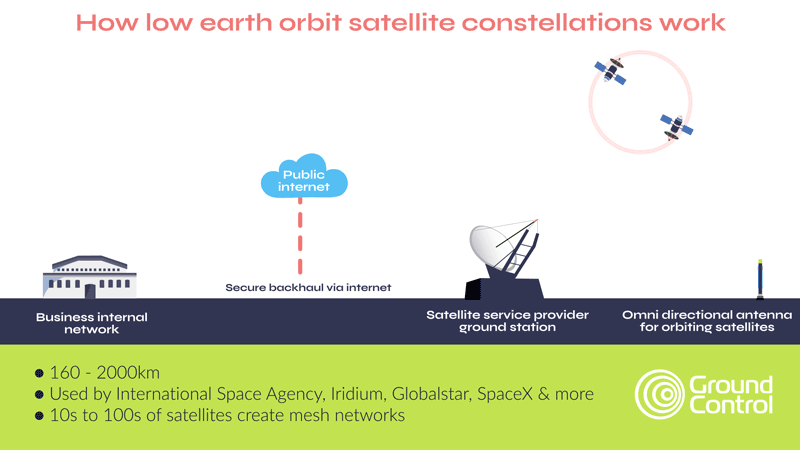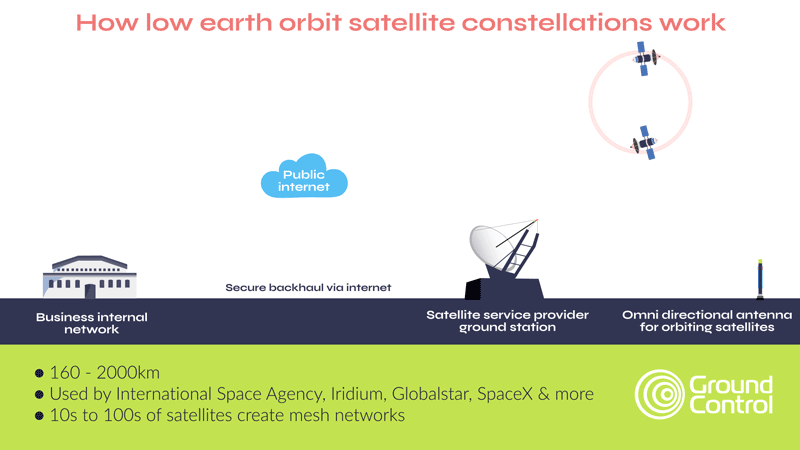
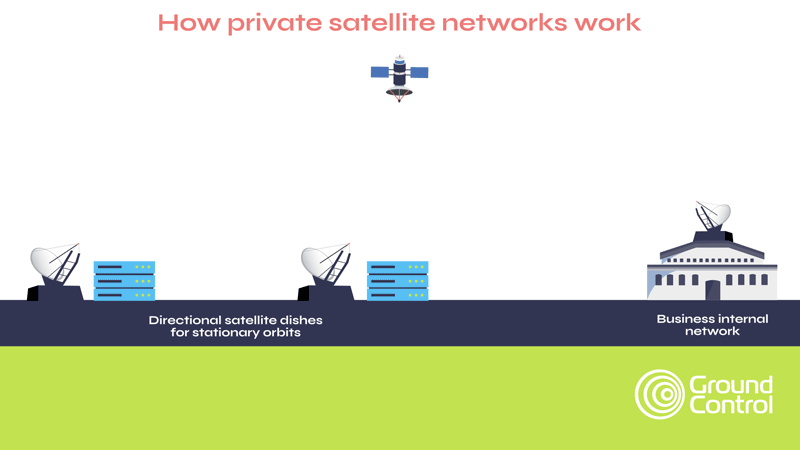
Critical National Infrastructure, however, often benefits from, and may even require, complete independence from public infrastructure, and that’s how private satellite networks like TSAT function. Here, as shown in the diagram below, data from the satellite comes to a ground station on your premises, rather than into the satellite network’s ground station. This means that your data is air gapped from external networks.
Part of the TSAT service is dedicated satellite bandwidth that prevents interference from other users, ensuring consistent and secure connectivity. TSAT also has no reliance on GPS timing, making it immune to GPS jamming. What’s more, its geo-redundant hubs and frequency diversity allow terminals to automatically switch frequencies if interference occurs, ensuring uninterrupted communication.
Real-World Applications of TSAT
A major energy infrastructure operator connects gas markets between the UK and continental Europe, managing a bi-directional gas pipeline with terminals in two key locations.
To maintain operations, a series of pressure and temperature sensors must continuously transmit data to the company’s SCADA system, which authorizes gas transmission.
If this sensor data becomes unavailable, production must halt, and gas venting procedures are required; an expensive process with significant operational and environmental impact.
To ensure real-time, reliable sensor data transmission, the company requires multiple active communication pathways at all times. They maintain a dedicated fiber connection alongside two satellite connections, all tasked with delivering critical data to the SCADA system. To further reduce reliance on public infrastructure, they have implemented TSAT ground stations at each terminal, eliminating the need for internet-based backhaul.

Each satellite link consists of two antennas: a hub and a remote. Typically, the remote antenna is positioned in a more isolated location near the sensors, transmitting data to the hub at the operations center. However, in this case, both satellite dishes are located in close proximity but pointed at different satellites, ensuring redundancy in case of a satellite failure.
Additionally, the company has implemented a unique failsafe: at each terminal, the hub and remote antennas are pointed at opposing satellites relative to the other terminal. This setup provides resilience against localized weather disruptions or signal degradation.
This system has been in place for over 16 years, with hardware upgrades along the way, and in that time, the satellite connectivity has never failed. Ground Control supports the company with a full turnkey service, including setup, training for routine maintenance, and periodic site visits for system health checks.
Embracing Satellite Technology for Cyber Defense
With the growing threats posed by cyber warfare, the time to act is now. TSAT offers a solution that is robust, resilient, and adaptable to the evolving threats of the digital age to utilities. It’s time for utility providers and organizations worldwide to adopt secure satellite enabled technologies, like TSAT, to protect their most vital assets and ensure uninterrupted services to customers. The question isn’t whether you can afford to adopt this technology – it’s whether you can afford not to.
Can we help?
Our satellite-enabled solutions offer robust security features designed to protect your critical data, coupled with reliable connectivity.
Partner with us to explore satellite solutions that safeguard your operations and enhance your secure data transfer capabilities.
Complete the form or email hello@groundcontrol.com and we’ll get back to you within one working day.
